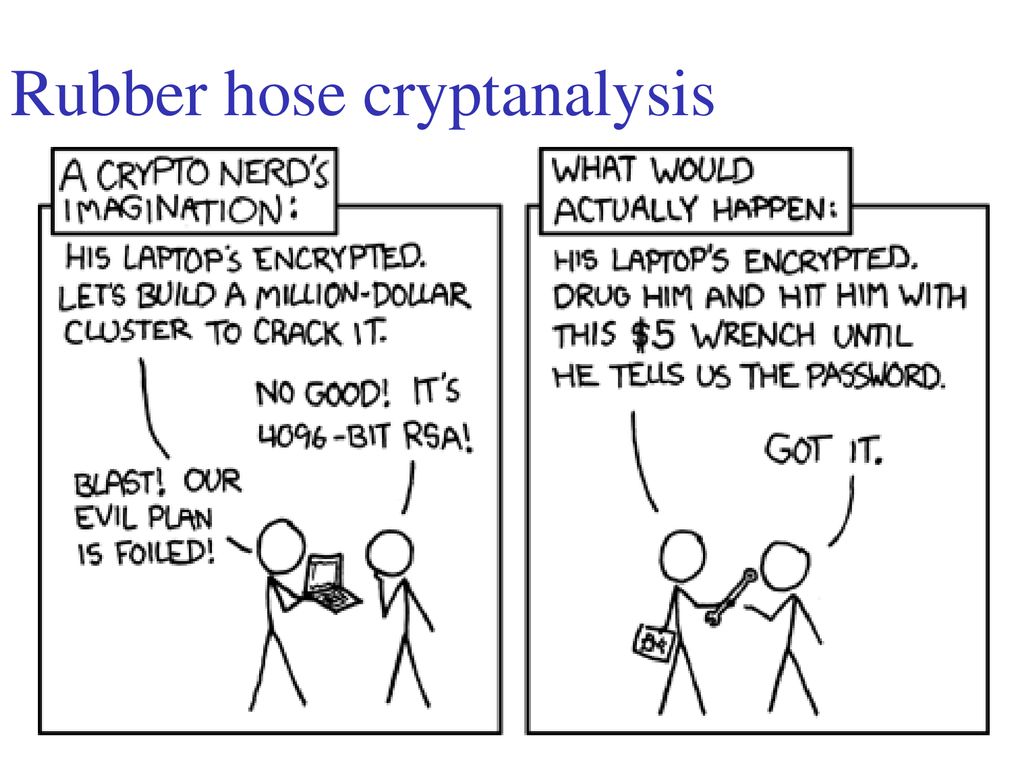
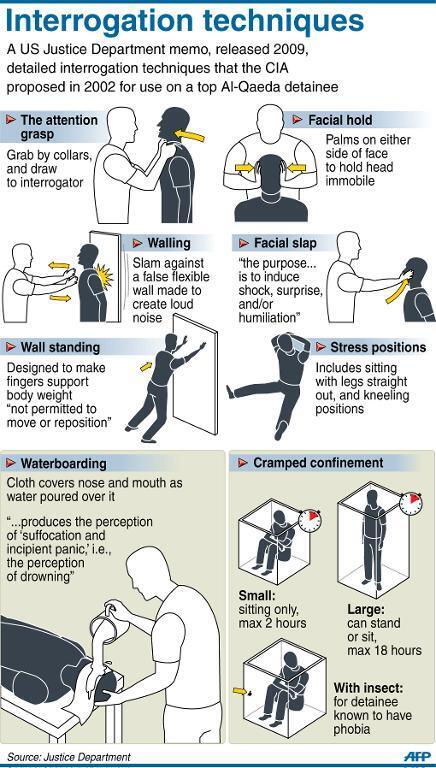
Russia :: mascot :: Rubber-hose cryptanalysis :: butilka :: shvabring :: Tulsky Pryanik :: Суровая правда :: countries / funny pictures & best jokes: comics, images, video, humor, gif animation - i lol'd

Articles on Torture, Including: Milgram Experiment, Psychology of Torture, Russian Roulette, Crucifixion, Crime Against Humanity, Castration, Room 101, Disembowelment, Electric Shock, Interrogation, Rubber-Hose Cryptanalysis, Impalement by Hephaestus ...

Neuroscience Meets Cryptography: Designing Crypto Primitives Secure Against Rubber Hose Attacks | USENIX

Anonymous Ghostwriters - Rubber Hose Cryptography works by filling the entire hard drive with random characters that are indistinguishable from encrypted data. The file system then takes each archive of real data

Russia :: mascot :: Rubber-hose cryptanalysis :: butilka :: shvabring :: Tulsky Pryanik :: Суровая правда :: countries / funny pictures & best jokes: comics, images, video, humor, gif animation - i lol'd

Neuroscience Meets Cryptography: Crypto Primitives Secure Against Rubber Hose Attacks | May 2014 | Communications of the ACM